Recovering lost files from a **backup image** can feel like navigating a maze, but with the right **software** and methodology, you can retrieve your **data** quickly and securely. Backup images are snapshots of entire disks or partitions, capturing operating system configurations, applications, and user **files**. By understanding how to work with these images effectively, you’ll ensure maximum **data** **integrity** and minimize downtime when disasters strike.
Understanding Backup Images and Their Role
A **backup** image is more than just a collection of files—it’s an exact bit-by-bit copy of a storage medium at a particular moment in time. Unlike incremental or differential backups that only record changes, a full disk **image** contains operating system files, system configuration, and every user data block. Key benefits include complete system **recovery**, streamlined migration to new hardware, and a reliable fallback after ransomware or hardware failures.
Types of backup images vary by software vendor, but they typically fall into three categories:
- Full Images: A complete copy of the entire disk or partition.
- Incremental Images: Captures changes since the last backup.
- Differential Images: Captures changes since the last full backup.
Choosing the right image format depends on your storage capacity, desired **efficiency**, and recovery time objectives. Some formats are proprietary and require the same vendor’s **software** for restoration, while others rely on open standards accessible through multiple tools.
Preparing the Environment for Restoration
Before diving into the restoration process, a well-prepared environment is crucial:
- Verify Backup Integrity: Use built-in verification tools or checksums to confirm that the backup image is not corrupted.
- Secure Storage Location: Ensure sufficient space on the destination drive and isolate it from the production environment to prevent accidental overwrites.
- Obtain Appropriate Software: Download and install the recovery **software** that supports your image format. Keep the version updated to handle new file systems and encryption schemes.
- Document Procedures: Create a step-by-step recovery plan with detailed instructions, contact numbers, and escalation paths.
Preparation reduces errors and speeds up the overall process. In critical situations, a previously tested recovery drill can cut restoration time by 30–50 percent.
Step-by-Step Restoration Process
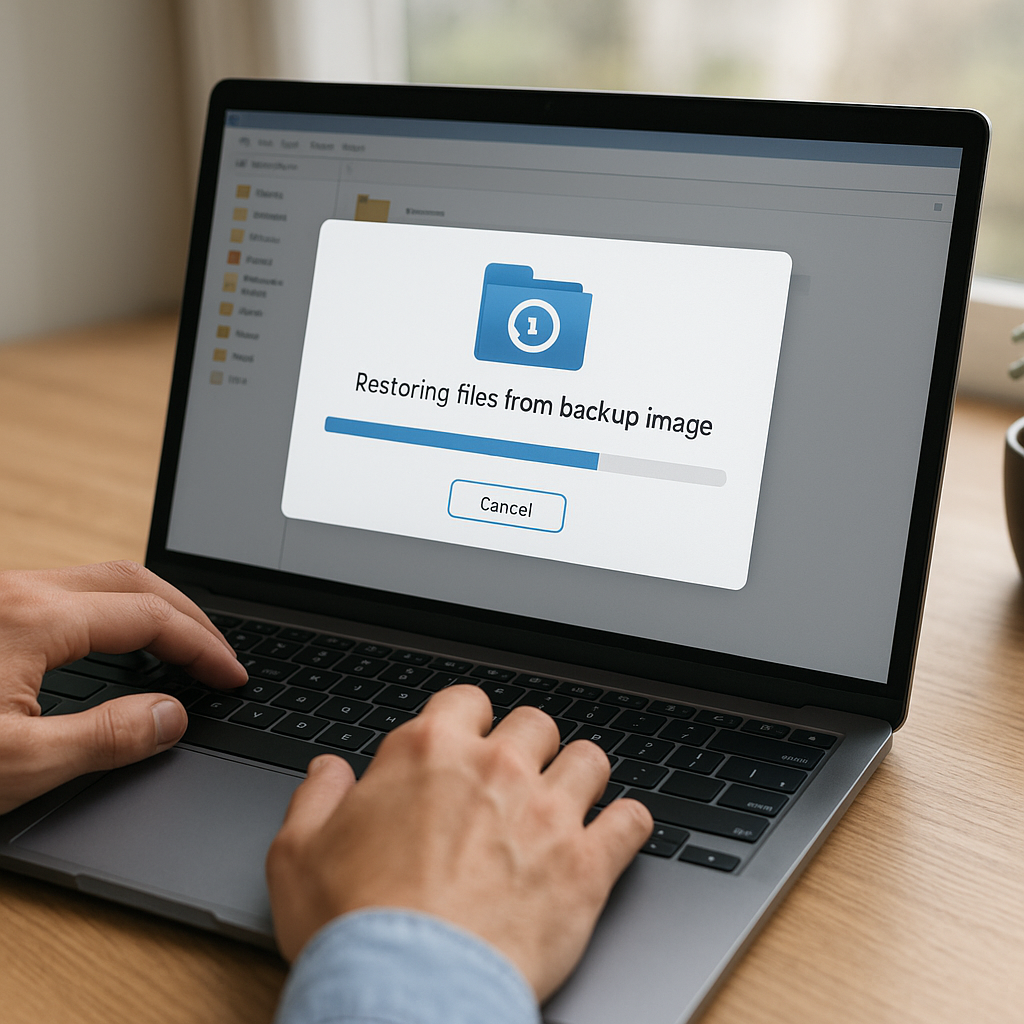
1. Mounting or Loading the Backup Image
First, launch your chosen recovery **software** and locate the option to mount or open a backup **image**. Some tools offer a virtual drive interface, allowing you to browse and extract **files** directly. Others require you to assign the image to a physical or virtual drive letter.
- Select the image from local or network storage.
- Enter encryption passwords if the image is protected.
- Choose whether to mount read-only to avoid unintended changes.
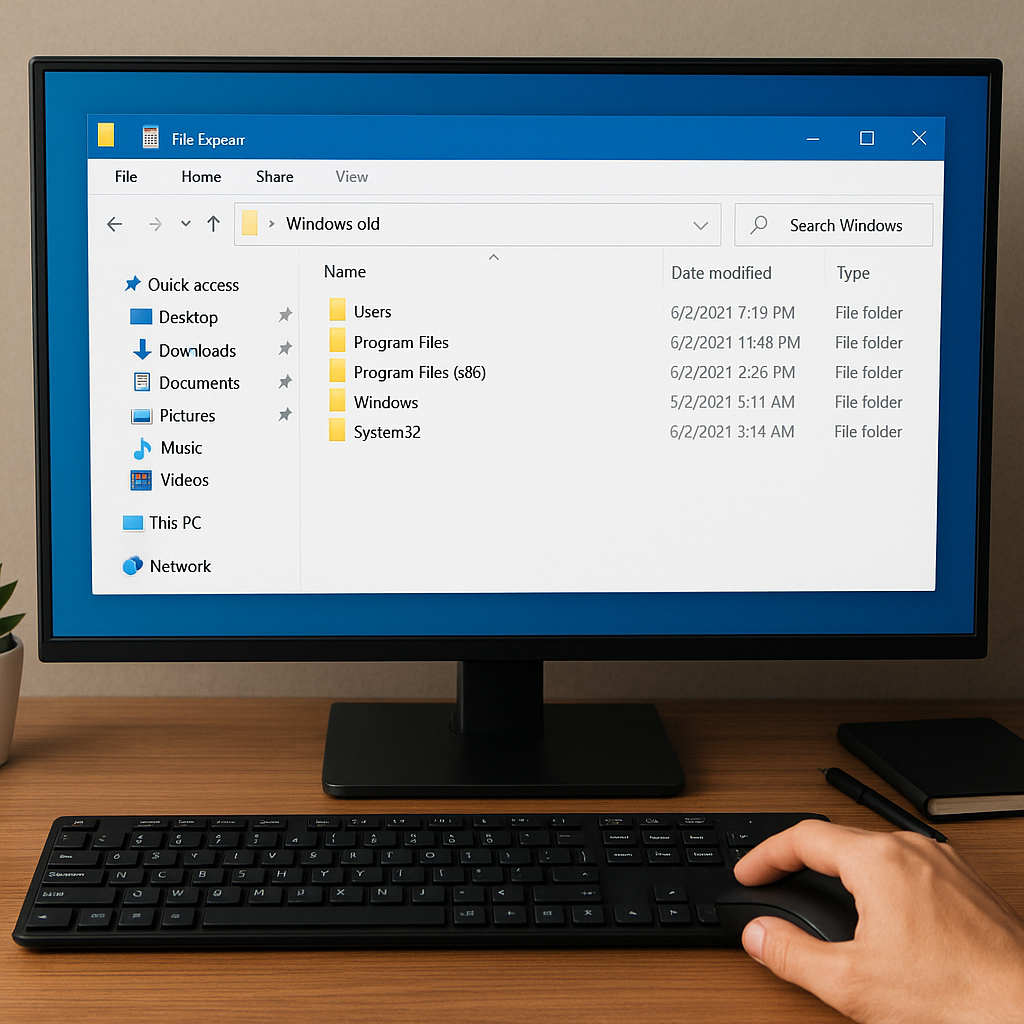
2. Browsing and Selecting Files
Once the image is mounted, navigate through the directory structure as if it were a live filesystem. Look for critical folders like C:Users or /home, depending on your operating system. You can selectively restore individual **files** or entire folders to save time and disk space.
3. Initiating the Restore Operation
With your targets identified, begin the restoration:
- Specify the destination path: You can restore to the original location (with caution) or to an alternate directory to prevent overwriting newer data.
- Adjust advanced options: Some **software** allows you to filter by date, file type, or size, and to preserve original timestamps.
- Start the process and monitor logs for warnings or errors.
Depending on the volume of data, the restoration may take from minutes to hours. Modern recovery **software** uses multi-threading to speed up transfers and reduce idle CPU cycles.
Verifying Recovery and Ensuring Data Consistency
Completing the restore operation isn’t the final step. You must verify that your **files** are intact and usable:
- Checksum Comparison: Generate MD5, SHA-1, or SHA-256 checksums of critical files and compare them with known good values.
- Application Testing: Launch restored applications or inspect configuration files to confirm compatibility and settings.
- User Acceptance: Ask end users to review their directories and validate important documents, media files, or databases.
Skimping on verification can lead to hidden corruption or incomplete **recovery**, which might manifest weeks later during critical operations.
Best Practices for Backup and Recovery
To maintain a robust disaster recovery plan, adhere to these industry **standards**:
- Implement a 3-2-1 backup strategy: Keep three copies of your data, on two different media, with one off-site.
- Regularly test your backup images by performing trial restores and integrity checks.
- Update your recovery **software** and operating system patches to address security vulnerabilities.
- Automate notifications to alert administrators of backup failures or degraded image health.
- Maintain clear documentation and train personnel in restoration procedures.
By following these guidelines, you’ll reduce downtime, protect against data loss, and ensure that you can confidently **restore** your environment whenever necessary.